Introduction
Bluetooth technology has transformed the way we connect and communicate with our devices. From wireless speakers to smart home gadgets, Bluetooth makes our lives easier and more connected. However, this convenience comes with a price: the potential for security and privacy breaches. Bluetooth signal jammers have emerged as a solution to protect against unauthorized Bluetooth communication, ensuring that sensitive information remains secure. In this comprehensive guide, we’ll delve into what Bluetooth signal jammers are, how they work, their applications, the reasons why people use them, and what you should consider before using them.
Key Facts About Bluetooth Jammers
- Function: Disrupts Bluetooth signals to prevent unauthorized data transmission or device pairing.
- Technology: Emits signals to interfere with Bluetooth frequencies.
- Legal Status: Check local laws for compliance.
- Applications: Personal privacy, corporate security, event protection.
- Effectiveness: Highly effective against common Bluetooth devices.
What is a Bluetooth Signal Jammer?
In the simplest terms, a Bluetooth jammer is a device designed to prevent Bluetooth-enabled devices from communicating with each other. It does this by creating intentional radio frequency interference, effectively creating a “dead zone” where Bluetooth signals cannot be sent or received.
Think of a quiet room where two people are trying to have a conversation. A jammer is like a third person standing between them, shouting loudly. The original conversation is drowned out by the noise, making communication impossible. Similarly, a Bluetooth jammer floods the specific radio frequencies used by Bluetooth with powerful, disruptive noise, preventing devices like wireless headphones, speakers, keyboards, and hidden eavesdropping devices from connecting or exchanging data.
The purpose of a Bluetooth signal jammer is to safeguard against unauthorized Bluetooth communication, including:
- Preventing unauthorized device pairing.
- Blocking Bluetooth data transfers.
- Protecting against Bluetooth-based surveillance or eavesdropping.
How Does Bluetooth Jamming Technology Work?
To understand how jamming works, you first need to understand how Bluetooth communicates. Bluetooth technology operates in the 2.4 GHz ISM (Industrial, Scientific, and Medical) radio band. To avoid interference from other devices using this crowded frequency (like Wi-Fi routers or microwave ovens), Bluetooth uses a clever technique called Frequency-Hopping Spread Spectrum (FHSS).
What is FHSS? Instead of transmitting on a single frequency, Bluetooth devices constantly and rapidly “hop” between 79 different channels within the 2.4 GHz band, changing frequencies up to 1600 times per second in a pseudo-random sequence known only to the paired devices. This makes the connection robust and difficult to intercept or disrupt. If one channel is noisy, the devices simply hop to the next clear one in the sequence.
How a Jammer Defeats FHSS: A Bluetooth jammer works on a brute-force principle. It doesn’t try to guess the hopping sequence. Instead, it transmits a powerful “noise” signal across the entire 2.4 GHz band simultaneously. This barrage of interference effectively overwhelms all 79 channels, leaving no clear channel for the Bluetooth devices to hop to. The original, much weaker Bluetooth signal is completely buried in the noise, and the connection is broken.
Types of Bluetooth Signal Jammers
-
Portable Bluetooth Jammers
These are small, battery-powered devices that can be easily carried in a pocket or bag. They are ideal for personal use, providing protection on the go, whether you’re in a public space or during private discussions where Bluetooth devices might be present.
-
Fixed Bluetooth Jammers
Designed for permanent installation, fixed Bluetooth signal jammers are typically used in sensitive areas like conference rooms, secure facilities, or government offices. These devices offer continuous protection against Bluetooth eavesdropping, ensuring that sensitive discussions remain confidential.
-
Multi-Frequency Jammers
Some advanced jammers can disrupt multiple wireless signals, including Bluetooth, Wi-Fi, and cellular. This comprehensive approach provides security against various forms of surveillance, making them suitable for environments where multiple wireless technologies are in use.
Why People Use Bluetooth Jammers
- Privacy Protection: With the increasing prevalence of Bluetooth-enabled devices, individuals and organizations are seeking ways to protect their conversations and data from being recorded or transmitted without consent.
- Data Security: Bluetooth signal jammers provide a layer of security against unauthorized access to personal or corporate data through Bluetooth connections, reducing the risk of data breaches.
- Corporate Espionage Prevention: In a corporate setting, Bluetooth signal jammers are used to prevent competitors or malicious insiders from stealing sensitive information or recording confidential meetings.
- Preventing Bluetooth Tracking: Many modern devices use Bluetooth for location tracking. Bluetooth signal jammers can prevent unauthorized tracking, ensuring personal privacy.
- Compliance with Regulations: In some cases, using Bluetooth signal jammers might be required to comply with regulations or security protocols, especially in sectors dealing with highly sensitive information.
- Securing Events: Events often involve high-profile individuals or sensitive information. Bluetooth signal jammers ensure that these events remain secure from unauthorized recordings or data transfers.
- Protection Against Surveillance: With concerns about surveillance increasing, Bluetooth signal jammers provide a means to protect against potential eavesdropping or spying via Bluetooth devices.
DIY “Jammers” vs. Professional Wireless Security Solutions
A quick online search reveals countless guides for building a “DIY Bluetooth Jammer.” While these projects can be interesting experiments for hobbyists, it’s crucial to understand the vast and critical differences between a homemade device and a professional-grade wireless security solution. For any serious application, relying on a DIY tool is not just ineffective—it’s a significant security and operational risk. Let’s break down why.
| Feature | DIY Jammer | Professional Solution |
|---|---|---|
| Target Frequencies | ✗ Typically targets a single, narrow band (e.g., only 2.4 GHz) with poor precision. |
✓ Multi-band coverage by design, precisely targeting Bluetooth, Wi-Fi, and Cellular (2G/3G/4G/5G) signals simultaneously. |
| Effectiveness & Power | ✗ Low power output, unstable signal, and often ineffective against modern protocols like Bluetooth’s Frequency-Hopping (FHSS). |
✓ High, stable power output with sophisticated signal generation to guarantee disruption of all targeted protocols, including FHSS. |
| Reliability & Safety | ✗ No shielding, prone to overheating, and can interfere with unintended critical services (e.g., medical devices, emergency radios). |
✓ Professionally engineered with proper heat management, RF shielding, and continuous 24/7 operation. |
| Legality & Compliance | ✗ Illegal to operate in most countries for civilian use. No compliance with telecommunication regulations. |
✓ Supplied exclusively to authorized government, military, and law enforcement entities under strict legal frameworks. |
| Scope of Use | ✗ Hobbyist experimentation or attempting to solve a minor, temporary annoyance. |
✓ Mission-critical security: protecting sensitive government meetings, securing correctional facilities, neutralizing IED threats, and corporate counter-espionage. |
Professional Applications for Wireless Signal Control
Professional wireless security solutions are not for public use; they are precision tools designed for specific, high-stakes environments where information security is paramount. These systems are exclusively deployed for authorized entities to protect critical assets. Here are the primary application scenarios:
🏢Corporate Security
Protecting intellectual property and confidential conversations within sensitive areas like boardrooms, R&D labs, and executive offices. These systems prevent unauthorized recording or data exfiltration via Bluetooth, Wi-Fi, or cellular-enabled eavesdropping devices.
🔒Secure Facilities
Enforcing “no communication” policies in high-security environments such as prisons, correctional facilities, and sensitive government buildings. The primary goal is to prevent inmates or unauthorized personnel from using contraband cell phones or other wireless devices.
🚗Vehicle Security
Protecting high-value individuals or convoys from being tracked or eavesdropped on via hidden Bluetooth GPS trackers or microphones. This is a common application for executive protection and secure transportation details.
iSecus’s Professional Wireless Signal Jammer, not ONLY block Bluetooth
The signal jammer we offer is Multi-Frequency Jammer. DT-510 is a top-level portable Wireless Signal Jammer adopted SDR (Signal Defines Radio) technology. It is a revolutionary device that ensures a secure communication environment. By effectively jamming mobile networks, Bluetooth and WIFI signals, it offers an additional layer of security to your communication framework.
It is also called All-standard Signal Jamming device: Supports signal jamming for 2G/3G/4G/5G mobile networks, 2.4G Bluetooth devices, 2.4G/5.2G/5.8G WIFI wireless devices, commonly used remote controls, etc. It supports flexible settiing about the radio frequency bands to be jammed, accoring to different applicational requirement.
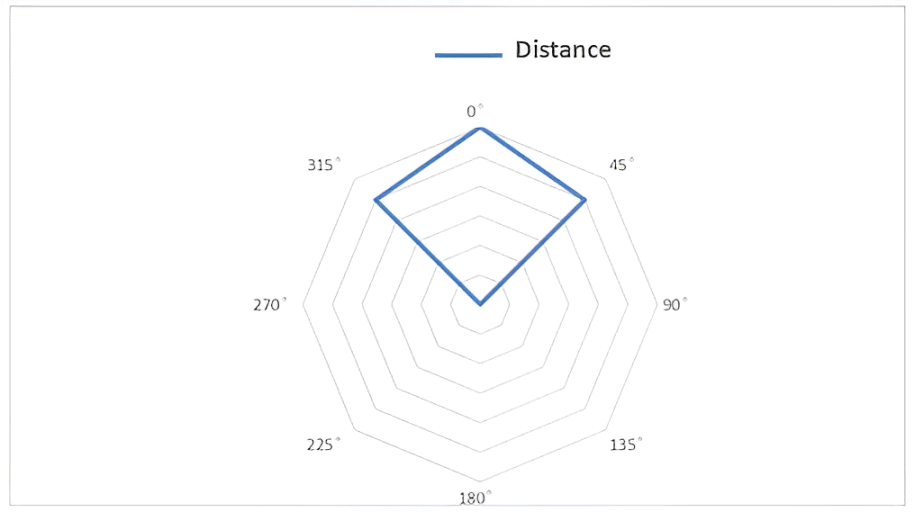
What is the jamming distance of DT-510?
- High power: facing distance 10-12m, 120° sideline distance 6-8m
- Medium power: facing distance 8-10m, 120° sideline distance 4-6m
- Low power: facing distance 6-8m, 120° sideline distance 3-5m
What is the jamming range of DT-510?
Under an unshielded environment, it can support a covering area 60 m²-80m² (RSRP less than -85 dBm ~ -90 dBm). When radio frequency signal hits walls, it will reflect to other direction. So for a regular meeting room/class room, installing 1pc DT-510 Wireless Signal Jammer can meet the requirement.
Typical Applications of DT-510 Wireless Signal Jammer
1. Corporate Security and Confidential Meetings
- Scenario: A high-level executive team is conducting a confidential board meeting in a corporate office. To prevent potential eavesdropping or data leaks via Bluetooth-enabled devices (e.g., hidden recording devices, smartphones, or wireless microphones), a Bluetooth jammer is activated in the meeting room.
- Purpose: Ensures that sensitive discussions remain private and protected from unauthorized surveillance.
2. Examination Halls and Academic Integrity
- Scenario: During a critical university examination, students are prohibited from using Bluetooth-enabled devices to communicate or access external resources. A Bluetooth jammer is deployed in the examination hall to block all Bluetooth signals, preventing cheating via wireless earpieces or smartwatches.
- Purpose: Maintains the integrity of the examination process and ensures fair results.







